Amazon on Friday said it flagged and disrupted what it described as an opportunistic watering hole campaign orchestrated by the Russia-linked APT29 actors as part of their intelligence gathering efforts.
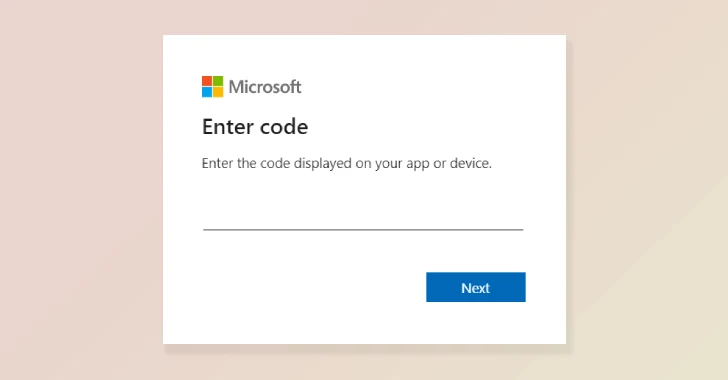
The campaign used “compromised websites to redirect visitors to malicious infrastructure designed to trick users into authorizing attacker-controlled devices through Microsoft’s device code authentication flow,” Amazon’s Chief Information Security Officer CJ Moses said.
APT29, also tracked as BlueBravo, Cloaked Ursa, CozyLarch, Cozy Bear, Earth Koshchei, ICECAP, Midnight Blizzard, and The Dukes, is the name assigned to a state-sponsored hacking group with ties to Russia’s Foreign Intelligence Service (SVR).
In recent months, the prolific threat actor has been linked to attacks leveraging malicious Remote Desktop Protocol (RDP) configuration files to target Ukrainian entities and exfiltrate sensitive data.
Since the start of the year, the adversarial collective has been observed adopting various phishing methods, including device code phishing and device join phishing, to obtain unauthorized access to Microsoft 365 accounts.
As recently as June 2025, Google said it observed a threat cluster with affiliations to APT29 weaponizing a Google account feature called application-specific passwords to gain access to victims’ emails. The highly targeted campaign was attributed to UNC6293.
The latest activity identified by Amazon’s threat intelligence team underscores the threat actor’s continued efforts to harvest credentials and gather intelligence of interest, while simultaneously sharpening their tradecraft.
“This opportunistic approach illustrates APT29’s continued evolution in scaling their operations to cast a wider net in their intelligence collection efforts,” Moses said.
The attacks involved APT29 compromising various legitimate websites and injecting JavaScript that redirected approximately 10% of visitors to actor-controlled domains, such as findcloudflare[.]com, that mimicked Cloudflare verification pages to give an illusion of legitimacy.
In reality, the end goal of the campaign was to entice victims into entering a legitimate device code generated by the threat actor into a sign-in page, effectively granting them access to their Microsoft accounts and data. This technique was detailed by both Microsoft and Volexity back in February 2025.
The activity is also noteworthy for incorporating various evasion techniques, such as Base64 encoding to conceal malicious code, setting cookies to prevent repeated redirects of the same visitor, and shifting to new infrastructure when blocked.
Amazon told The Hacker News that it doesn’t have additional information on how many websites were compromised as part of this effort, and how these sites were hacked in the first place. The tech giant also noted that it was able to link the domains used in this campaign with infrastructure previously attributed to APT29.
“Despite the actor’s attempts to migrate to new infrastructure, including a move off AWS to another cloud provider, our team continued tracking and disrupting their operations,” Moses said. “After our intervention, we observed the actor register additional domains such as cloudflare.redirectpartners[.]com, which again attempted to lure victims into Microsoft device code authentication workflows.”