Researchers at Arctic Wolf Labs have discovered a cyber espionage campaign targeting European diplomatic entities in Hungary, Belgium and additional European nations.
The activity was observed in September and October 2025 and attributed to UNC6384, a cluster likely linked to Chinese-affiliated group Mustang Panda, also known as TEMP.Hex.
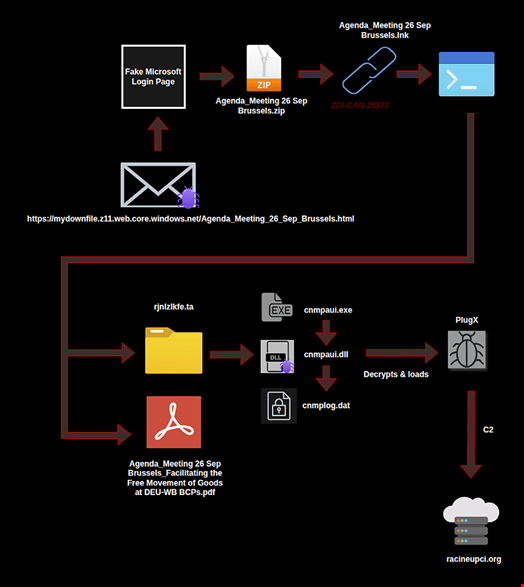
The campaign included refined social engineering leveraging authentic diplomatic conference themes as well as the exploitation of ZDI-CAN-25373, a Windows shortcut vulnerability disclosed in March 2025, said an Arctic Wolf report, published on October 30.
The threat actor deployed a multi-stage malware chain and involved the PlugX remote access trojan (RAT), a malicious payload typical of Chinese -affiliated threat actors.
Attack Chain: Spear Phishing, Windows Exploit and PlugX RAT Deployment
The attack begins with targeted spear phishing emails themed around diplomatic meetings and conferences.
These spear phishing emails lead to the delivery of malicious LNK files, which exploit ZDI-CAN-25373, a Windows shortcut vulnerability that allows the threat actor to execute commands covertly by adding whitespace padding within the COMMAND_LINE_ARGUMENTS structure.
When executed, the LNK file invokes PowerShell with an obfuscated command that decodes a tar archive file named rjnlzlkfe.ta, which it saves it to the AppDataLocalTemp directory. The PowerShell command then extracts the tar archive using tar.exe -xvf and initiates execution of the contained cnmpaui.exe file.
In parallel, each LNK file opened a decoy PDF document using diplomatic conference themes as lures, including Agenda_Meeting 26 Sep Brussels.lnk, which references a European Commission meeting on facilitating the free movement of goods at EU-Western Balkans border crossing points that was scheduled for September 26, 2025, in Brussels.
The extracted tar archive contains three critical files that enable the attack chain through DLL side-loading, a technique that abuses the Windows DLL search order to load malicious code through legitimate applications.
These include a legitimate Canon printer assistant utility that possesses a digital signature from Canon Inc., signed with a certificate issued by Symantec Class 3 SHA256 Code Signing CA. While the certificate has been expired since 2018, it is still recognized by Windows.
The second file, cnmpaui.dll, serves as a lightweight loader designed to decrypt and execute the third file in the archive, cnmplog.dat, which contains the encrypted PlugX payload.
First observed in 2008, PlugX is a RAT that is actively deployed by Chinese-affiliated threat actors.
The malware provides comprehensive remote access capabilities including command execution, keylogging, file upload and download operations, persistence establishment and extensive system reconnaissance functions. Its modular architecture allows operators to extend functionality through plugin modules tailored to specific operational requirements.
PlugX operates under multiple aliases including Korplug, TIGERPLUG and SOGU.
UNC6384’s Growing Sophistication and Geographic Expansion
UNC6384 is a Chinese-linked cyber espionage group identified by Google’s Threat Intelligence Group (GTIG) in August 2025.
The threat group primarily targets diplomatic entities, initially focusing on Southeast Asia before expanding to European diplomats.
It uses sophisticated attack chains involving social engineering, traffic manipulation, signed malicious downloaders and memory-based malware to evade detection and achieve its goals.
A key tool in UNC6384’s arsenal is PlugX, tracked by Google as SOGU.SEC when used by this group.
Google assessed that UNC6384 is linked to Mustang Panda, a well-known China-aligned threat actor.
Both groups share targeting patterns (focus on government sectors) along with overlapping command-and-control (C2) infrastructure, PlugX variants and DLL side-loading techniques.
In this new malicious campaign detected by Arctic Wolf, targets included Hungarian and Belgian diplomats and potentially Serbian government officials. Arctic Wolf cited additional research by StrikeReady documenting the targeting of Serbian government aviation departments using lures themed around flight training plans for October 2025.
Arctic Wolf Labs researchers noted that this new UNC6384 campaign highlights the threat actor’s growing sophistication and geographic expansion in cyber espionage against diplomatic targets.
They emphasized that the group weaponized ZDI-CAN-25373 just six months after its disclosure, showing a “sustained ability to integrate exploits into its tradecraft.”
The shift from Southeast Asia to European diplomats suggests either “broadened intelligence priorities” or the deployment of new regional teams, while still relying on centrally developed tools.
