By the middle of May, users around the world started to receive messages from their contacts through different instant-messaging applications, such as Skype and Gtalk – an attack that showed off how age-old techniques can ensnare thousands of users. Here, we analyze this attack.
Massive malware attacks have a huge impact on users. First of all, such attacks leave them vulnerable and unprotected. Secondly, they show the ability of cybercriminals to re-use old techniques that continue to ensnare thousands of users. By the middle of May, users around the world started to receive messages from their contacts through different instant-messaging applications, such as Skype and Gtalk.
With respect to malware propagation, there is a life cycle from one campaign carried out by the attacker to the next. During this variable period of time, the effectiveness of the attack usually changes, reaching a maximum effectiveness level, either due to the volume of infected victims or the number of people who received the threat.
When the volume of potential victims who receive the same threat through the same propagation channel over a short time period rises over a certain threshold, we can see chain reactions that exceed the attacker’s target and start to reach people outside the group of users who were chosen as possible victims.
Many of these factors came together on May 20th, when, as well as notifications from the ESET Early Warning System, we got queries from affected computer users and even received messages from contacts that members of the ESET Latin America’s Laboratory had associated with their Skype accounts. This behavior was one of the first indicators that analysis of the threat was necessary, so that we were able to alert users in the region about the appearance of a new worm which was spreading massively throughout the area and, most likely, into the rest of the world.
On May 20th, the Internet was flooded with messages propagated through Skype, which invited users to see a photograph that had been uploaded to different social networks. The links redirecting the user to the threat had been shortened with the Google URL-address shortener, so those who followed them would be tricked into downloading an archive with the malicious code.
This threat was detected by ESET Smart Security as a variant of Win32/Kryptik.BBKB, and it managed to lure more than 300,000 users into clicking on the messages and unexpectedly downloading the threat.
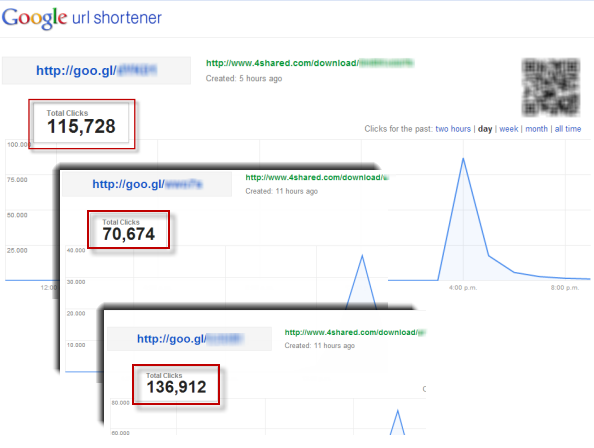
The impact in the first hours of the attack and the high volumes of users taken in by social engineering were reflected in the URL-address shortening system statistics, as can be seen in the following image:
Figure 1 – Propagation of malicious links during May 20th.
Moreover, what had initially been detected by the advanced heuristics of ESET’s products, was identified after the initial analysis in the Laboratory as a variant of Win32/Gapz, a powerful bootkit previously analyzed by ESET’s Labs and having the ability to inject itself into the explorer.exe process in order to gain control of the system. After a more thorough analysis, it was determined that the threat was in fact the PowerLoader dropper .
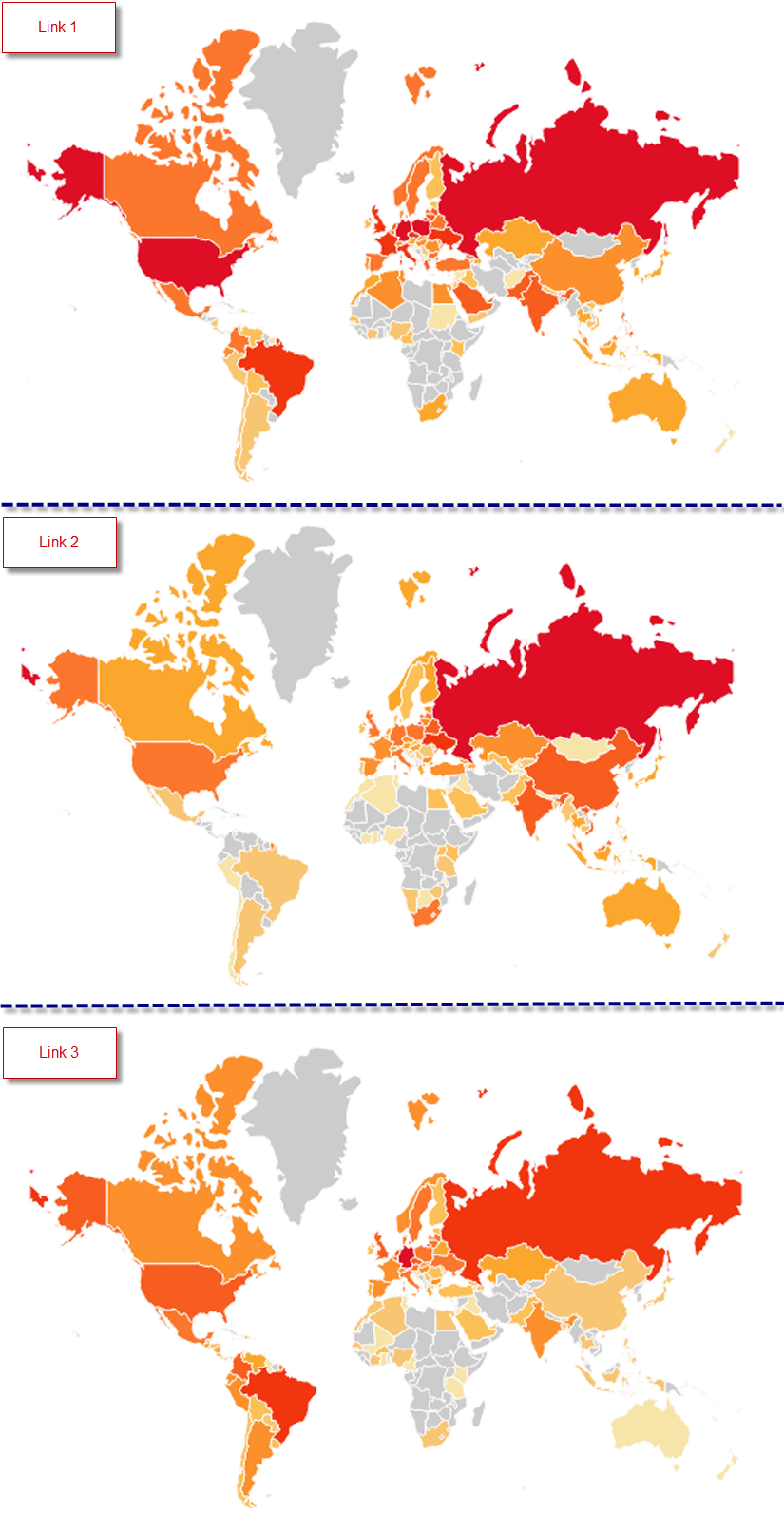
Out of the total number of clicks, 27% came from a Latin American country: the first three are Mexico (27,023), Brazil (37,757) and Colombia (54,524). Regarding other affected countries, particularly noteworthy are Russia, with a total of 41,107, and Germany, which is in the first place globally with 84,817 clicks during this first wave.
The message used by the infected computers varied from time to time, but all the victims’ contacts received a similar message to the one shown in the image below:
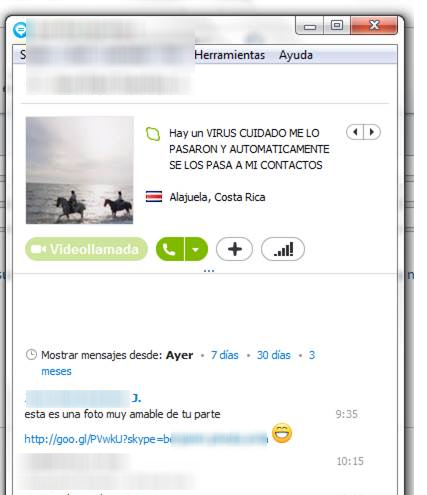
Figure 3 – Propagation message spread by a user infected with Win32/Rodpicom
In the days following the first wave of messages, the cybercriminals responsible for this attack kept on using different messages and new variants of their malware. This did not increase the number of users becoming victims of the deception, as was expected, but it did generate new and different messages.
By looking at the propagation graphics and statistics, it was almost certain that the most affected countries are not Latin American: however, thousands of users were being deceived by messages that were not even meant for them and who were becoming infected with a single click, thus spreading the malware to all their contacts.
The “Skype worm” proved to have a high propagation rate, spreading almost exponentially during the first days of operation, unsurprisingly since as each new person became a victim, all his or her contacts on Skype, Gtalk and other instant messaging systems received these same malicious links.
The two main threats involved corresponded to variants of Win32/PowerLoader, which infects the system and reports back to the C&C (Command and Control Panel), and Win32/Rodpicom, a worm that is able to spread through different instant messaging applications. If you would like to find more details about the threats used in this attack, we suggest you to take a look to the full article.
The combining of multiple threats into one single attack is not a novelty, but once again it proved to be extremely effective. Furthermore, each component of the pieces of malware involved had a specific function.
The events that took place between May 20th and the first days of June showed that techniques that are many years old can still be effective enough to cause damage. Different organizations found out that their security solutions were vulnerable, receiving warnings in large quantities but having no understanding of what was going on until the picture gradually cleared and the threats were identified. We’ve put all the information we gathered during our analysis into an article than you can download from here.
Cybercriminals do not need to reinvent the wheel for every attack: unfortunately they only need to combine malicious pieces of code in the right way and to trick the average user into double-clicking on it.
Acknowledgments
Thanks to Matias Porolli, Joaquin Rodriguez Varela, André Goujon and Sebastian Bortnik
Pablo Ramos
Security Researcher