| Source: Securonix |
Cybersecurity researchers have disclosed details of a new campaign dubbed PHALT#BLYX that has leveraged ClickFix-style lures to display fixes for fake blue screen of death (BSoD) errors in attacks targeting the European hospitality sector.
The end goal of the multi-stage campaign is to deliver a remote access trojan known as DCRat, according to cybersecurity company Securonix. The activity was detected in late December 2025.
“For initial access, the threat actors utilize a fake Booking.com reservation cancellation lure to trick victims into executing malicious PowerShell commands, which silently fetch and execute remote code,” researchers Shikha Sangwan, Akshay Gaikwad, and Aaron Beardslee said.
The starting point of the attack chain is a phishing email impersonating Booking.com that contains a link to a fake website (e.g., “low-house[.]com”). The messages warn recipients of unexpected reservation cancellations, urging them to click the link to confirm the cancellation.
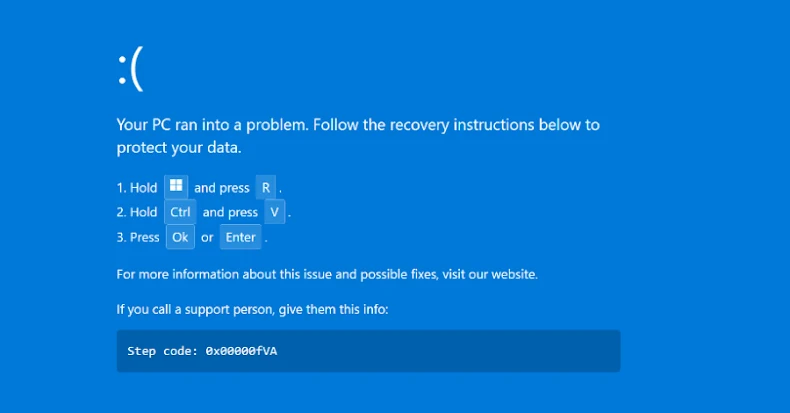
The website to which the victim is redirected masquerades as Booking.com, and serves a fake CAPTCHA page that leads them to a bogus BSoD page with “recovery instructions” to open the Windows Run dialog, paste a command, and press the Enter key. In reality, this results in the execution of a PowerShell command that ultimately deploys DCRat.
Specifically, this entails a multi-step process that commences with the PowerShell dropper downloading an MSBuild project file (“v.proj”) from “2fa-bns[.]com”, which is then executed using “MSBuild.exe” to run an embedded payload responsible for configuring Microsoft Defender Antivirus exclusions to evade detection, setting up persistence on the host in the Startup folder, and launching the RAT malware after downloads it from the same location as the MSBuild project.
It’s also capable of disabling the security program altogether if found to be running with administrator privileges. If it doesn’t have elevated rights, the malware enters a loop that triggers a Windows User Account Control (UAC) prompt every two seconds for three times in hopes that the victim will grant it the necessary permissions out of sheer frustration.
In tandem, the PowerShell code takes steps to open the legitimate Booking.com admin page in the default browser as a distraction mechanism and to give an impression to the victim that the action was legitimate.
DCRat, also called DarkCrystal RAT and a variant of AsyncRAT, is an off-the-shelf .NET trojan that can harvest sensitive information and expand its functionality by means of a plugin-based architecture. It’s equipped to connect to an external server, profile the infected system, and await incoming commands from the server, enabling the attackers to log keystrokes, run arbitrary commands, and deliver additional payloads like a cryptocurrency miner.
The campaign is an example of how threat actors are leveraging living-off-the-land (LotL) techniques, such as abusing trusted system binaries like “MSBuild.exe,” to move the attack to the next stage, establish a deeper foothold, and maintain persistence within compromised hosts.
“The phishing emails notably feature room charge details in Euros, suggesting the campaign is actively targeting European organizations,” Securonix said. “The use of the Russian language within the ‘v.proj’ MSBuild file links this activity to Russian threat factors using DCRat.”
“The use of a customized MSBuild project file to proxy execution, coupled with aggressive tampering of Windows Defender exclusions, demonstrates a deep understanding of modern endpoint protection mechanisms.”