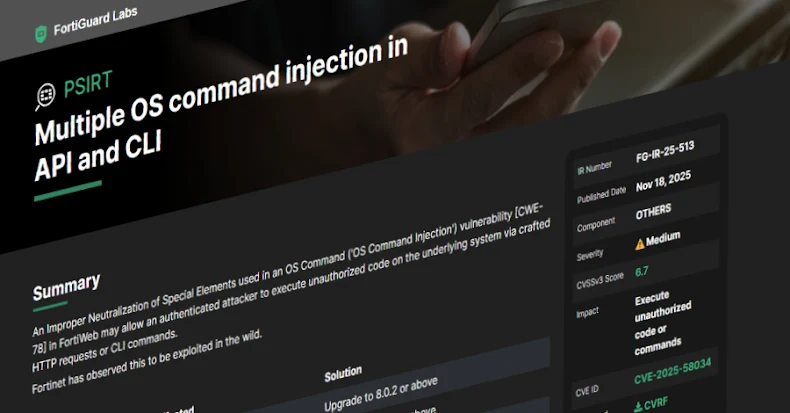
Fortinet has warned of a new security flaw in FortiWeb that it said has been exploited in the wild.
The medium-severity vulnerability, tracked as CVE-2025-58034, carries a CVSS score of 6.7 out of a maximum of 10.0.
“An Improper Neutralization of Special Elements used in an OS Command (‘OS Command Injection’) vulnerability [CWE-78] in FortiWeb may allow an authenticated attacker to execute unauthorized code on the underlying system via crafted HTTP requests or CLI commands,” the company said in a Tuesday advisory.
In other words, successful attacks require an attacker to first authenticate themselves through some other means and chain it with CVE-2025-58034 to execute arbitrary operating system commands.
It has been addressed in the following versions –
- FortiWeb 8.0.0 through 8.0.1 (Upgrade to 8.0.2 or above)
- FortiWeb 7.6.0 through 7.6.5 (Upgrade to 7.6.6 or above)
- FortiWeb 7.4.0 through 7.4.10 (Upgrade to 7.4.11 or above)
- FortiWeb 7.2.0 through 7.2.11 (Upgrade to 7.2.12 or above)
- FortiWeb 7.0.0 through 7.0.11 (Upgrade to 7.0.12 or above)
The company credited Trend Micro researcher Jason McFadyen for reporting the flaw under its responsible disclosure policy.
Interestingly, the development comes days after Fortinet confirmed that it silently patched another critical FortiWeb vulnerability (CVE-2025-64446, CVSS score: 9.1) in version 8.0.2. Although the company has not clarified if the exploitation activity is linked, Orange Cyberdefense said it observed “several exploitation campaigns” chaining CVE-2025-58034 with CVE-2025-64446 to facilitate authentication bypass and command injection.
“The timeline for both vulnerabilities being disclosed is only days apart. Both vulnerabilities were patched by the vendor in prior product updates and with no disclosure at the time of patching,” cybersecurity company Rapid7 said.
“There is an obvious utility of chaining an authentication bypass to an authenticated command injection. Given all of these things, it seems highly likely these two vulnerabilities comprise an exploit chain for unauthenticated remote code execution against vulnerable FortiWeb devices.”
“We activated our PSIRT response and remediation efforts as soon as we learned of this matter, and those efforts remain ongoing,” a Fortinet spokesperson told The Hacker News. “Fortinet diligently balances our commitment to the security of our customers and our culture of responsible transparency.”
It’s currently not clear why Fortinet opted to patch the flaws without releasing an advisory. But the move has left defenders at a disadvantage, effectively preventing them from mounting an adequate response.
“When popular technology vendors fail to communicate new security issues, they are issuing an invitation to attackers while choosing to keep that same information from defenders,” VulnCheck noted last week.
Update
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added the security defect to its Known Exploited Vulnerabilities (KEV) catalog, urging Federal Civilian Executive Branch (FCEB) agencies to patch it by November 25, 2025.