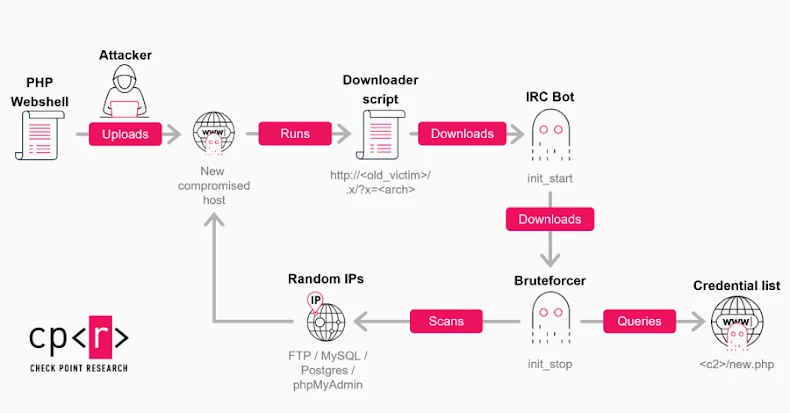
A new wave of GoBruteforcer attacks has targeted databases of cryptocurrency and blockchain projects to co-opt them into a botnet that’s capable of brute-forcing user passwords for services such as FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux servers.
“The current wave of campaigns is driven by two factors: the mass reuse of AI-generated server deployment examples that propagate common usernames and weak defaults, and the persistence of legacy web stacks such as XAMPP that expose FTP and admin interfaces with minimal hardening,” Check Point Research said in an analysis published last week.
GoBruteforcer, also called GoBrut, was first documented by Palo Alto Networks Unit 42 in March 2023, documenting its ability to target Unix-like platforms running x86, x64, and ARM architectures to deploy an Internet Relay Chat (IRC) bot and a web shell for remote access, along with fetching a brute-force module to scan for vulnerable systems and expand the botnet’s reach.
A subsequent report from the Black Lotus Labs team at Lumen Technologies in September 2025 found that a chunk of the infected bots under the control of another malware family known as SystemBC were also part of the GoBruteforcer botnet.
Check Point said it identified a more sophisticated version of the Golang malware in mid-2025, packing in a heavily obfuscated IRC bot that’s rewritten in the cross-platform programming language, improved persistence mechanisms, process-masking techniques, and dynamic credential lists.
The list of credentials includes a combination of common usernames and passwords (e.g., myuser:Abcd@123 or appeaser:admin123456) that can accept remote logins. The choice of these names is not happenstance, as they have been used in database tutorials and vendor documentation, all of which have been used to train Large language models (LLMs), causing them to produce code snippets with the same default usernames.
Some of the other usernames in the list are cryptocurrency-focused (e.g., cryptouser, appcrypto, crypto_app, and crypto) or target phpMyAdmin panels (e.g., root, wordpress, and wpuser).
“The attackers reuse a small, stable password pool for each campaign, refresh per-task lists from that pool, and rotate usernames and niche additions several times a week to pursue different targets,” Check Point said. “Unlike the other services, FTP brute-force uses a small, hardcoded set of credentials embedded in the bruteforcer binary. That built-in set points to web-hosting stacks and default service accounts.”
In the activity observed by Check Point, an internet-exposed FTP service on servers running XAMPP is used as an initial access vector to upload a PHP web shell, which is then used to download and execute an updated version of the IRC bot using a shell script based on the system architecture. Once a host is successfully infected, it can serve three different uses –
- Run the brute-force component to attempt password logins for FTP, MySQL, Postgres, and phpMyAdmin across the internet
- Host and serve payloads to other compromised systems, or
- Host IRC-style control endpoints or act as a backup command-and-control (C2) for resilience
Further analysis of the campaign has determined that one of the compromised hosts has been used to stage a module that iterates through a list of TRON blockchain addresses and queries balances using the tronscanapi[.]com service to identify accounts with non-zero funds. This indicates a concerted effort to target blockchain projects.
“GoBruteforcer exemplifies a broader and persistent problem: The combination of exposed infrastructure, weak credentials, and increasingly automated tools,” Check Point said. “While the botnet itself is technically straightforward, its operators benefit from the vast number of misconfigured services that remain online.”
The disclosure comes as GreyNoise revealed that threat actors are systematically scanning the internet for misconfigured proxy servers that could provide access to commercial LLM services.
Of the two campaigns, one has leveraged server-side request forgery (SSRF) vulnerabilities to target Ollama’s model pull functionality and Twilio SMS webhook integrations between October 2025 and January 2026. Based on the use of ProjectDiscovery’s OAST infrastructure, it’s posited that the activity likely originates from security researchers or bug bounty hunters.
The second set of activity, starting December 28, 2025, is assessed to be a high-volume enumeration effort to identify exposed or misconfigured LLM endpoints associated with Alibaba, Anthropic, DeepSeek, Google, Meta, Mistral, OpenAI, and xAI. The scanning originated from IP addresses 45.88.186[.]70 and 204.76.203[.]125.
“Starting December 28, 2025, two IPs launched a methodical probe of 73+ LLM model endpoints,” the threat intelligence firm said. “In eleven days, they generated 80,469 sessions – systematic reconnaissance hunting for misconfigured proxy servers that might leak access to commercial APIs.”