Cybercriminals are helping traditional organized crime groups steal physical goods via cargo freight hijacking.
Researchers at cybersecurity firm Proofpoint recently identified active malicious campaigns involving hackers targeting the transportation industry, especially trucking and logistics companies, in North America.
Their infection technique of choice included leveraging remote monitoring management (RMM) tools and remote access software (RAS) to gain access to their victims’ systems.
Attack Chain: Social Engineering, RMM and Credential Harvesting
In a November 3 report, Proofpoint revealed that the threat cluster engaged in suspected cargo theft has been active since at least June 2025, with further evidence suggesting the group’s campaigns began as early as January 2025.
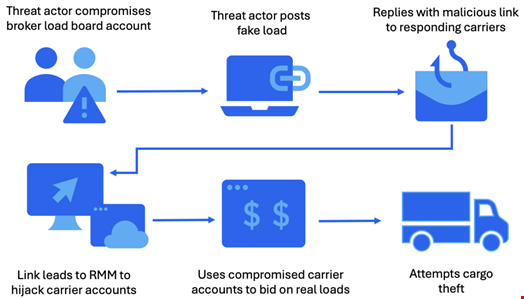
The typical attack chain starts with three social engineering tricks to get into the systems of infected targets. These include:
- Compromising load boards: the attacker posts fraudulent freight listings using compromised accounts on load boards and then sends emails containing malicious URLs to carriers who inquire about the loads
- Email thread hijacking: using compromised email accounts, the threat actors inject malicious content and URLs into existing conversations
- Direct targeting via email campaigns: the attacker launches direct email campaigns against larger entities, including asset-based carriers, freight brokerage firms and integrated supply chain providers. Gaining access to these entities may allow the actors to identify high-value freight loads or uncover other opportunities to further their objectives, such as posting fraudulent loads on load boards
The malicious emails contain URLs that lead to an executable (.exe) or an MSI (.msi) file, which, when clicked, installs an RMM tool, granting the threat actor full control of the compromised machine.
“In some cases, the threat actor will create domains and landing pages that impersonate legitimate brands or generic transportation terms to further the believability of the social engineering,” the Proofpoint researchers noted.
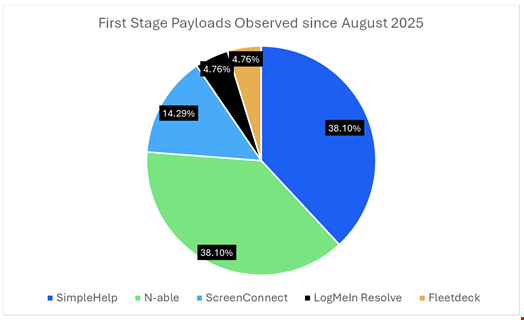
The RMM and RAS tools deployed on the targeted systems include ScreenConnect, SimpleHelp, PDQ Connect, Fleetdeck, N-able and LogMeIn Resolve – sometimes used in tandem.
Once initial access is established, the attacker conducts system and network reconnaissance and deploys credential harvesting tools, such as WebBrowserPassView.
“This activity indicates a broader effort to compromise accounts and deepen access within targeted environments,” the researchers wrote.
Overlaps with Previous Campaigns
The researchers identified related network infrastructure and similar tactics, techniques and procedures (TTPs) in campaigns delivering NetSupport and ScreenConnect going back to January 2025, “suggesting a longer operational timeline,” the Proofpoint report read.
These campaigns also showed some overlaps with malicious activity recorded between 2024 and March 2025, when a threat actor distributed a range of infostealers, including DanaBot, NetSupport, Lumma Stealer and StealC in the systems of ground transportation organizations.
However, the Proofpoint researchers could not confirm with high confidence whether these clusters of activity are related.
“All appear to have knowledge about the software, services and policies around how the cargo supply chain operates,” the researchers wrote.
The report also highlighted that, if these clusters of activity come from the same group, the use of RMM tools instead of infostealers in the latest campaigns could suggest a sophistication in the techniques employed.
“Stealers and RMMs serve the same purpose: remotely access the target to steal information. However, using RMM tools can enable threat actors to fly further under the radar. Threat actors can create and distribute attacker-owned remote monitoring tools and because they are often used as legitimate pieces of software, end users might be less suspicious of installing RMMs than other remote access trojans,” the Proofpoint researchers wrote.
“Additionally, such tooling may evade anti-virus or network detections because the installers are often signed, legitimate payloads distributed maliciously.”
Cyber-Enabled Cargo Theft, A Global Issue
Proofpoint has observed nearly two dozen campaigns targeting North American freight companies in September and October 2025, with volumes ranging from less than 10 to over 1000 messages per campaign.
The researchers also assessed “with high confidence” that this threat group collaborates with organized crime groups, who likely use their access to bid on cargo shipments and then steal and sell them.
In the report, Proofpoint also noted that while the latest observed campaigns targeted North American companies, cyber-enabled cargo thefts are rising across the world, including in freight hotspots like Brazil, Chile, Germany, India, Mexico, South Africa and the US.
According to the National Insurance Crime Bureau, cargo theft leads to $34bn in losses annually. Cyber intrusion techniques contributes significantly to these losses, said a July 2025 report by IMC Logistics and The American Trucking Associations.