Social media influencers can provide reach and trust for scams and malware distribution. Robust account protection is key to stopping the fraudsters.
It’s not an easy time to be an influencer. Brands are spending less, ad revenue is declining and competition is fierce – including from AI-generated influencers and impersonators. According to one study, around half of the industry makes just $15,000 or less per year, while just one in 10 pull in over $100,000. As if that wasn’t enough, there’s another challenge: influencers are an increasingly popular target for cybercriminals. A recent spear-phishing campaign abusing brands such as Tesla and Red Bull highlights the potential risks.
Account compromise could have a devastating impact, not only on the victim but also their followers and potential brand clients. If you’re a social media content creator, it may be time to revisit those account security best practices.
Why do influencers matter to hackers?
Threat actors are usually looking for several things in a potential online victim. If they’re on the hunt for influencer social media accounts to hijack, they’ll want ones with as many followers as possible. This means their scams or malware will be distributed far and wide. They ideally also want to target influencers who have built long-term trust with their audience, through months or years of providing advice online. Trust could also be earned through verified status badges. Either way, it means followers are more likely to click on the links in these accounts without thinking.
It goes without saying that hackers also need those accounts to be easy to compromise. Anything protected with a single weak password is a gift to an opportunistic cybercriminal.
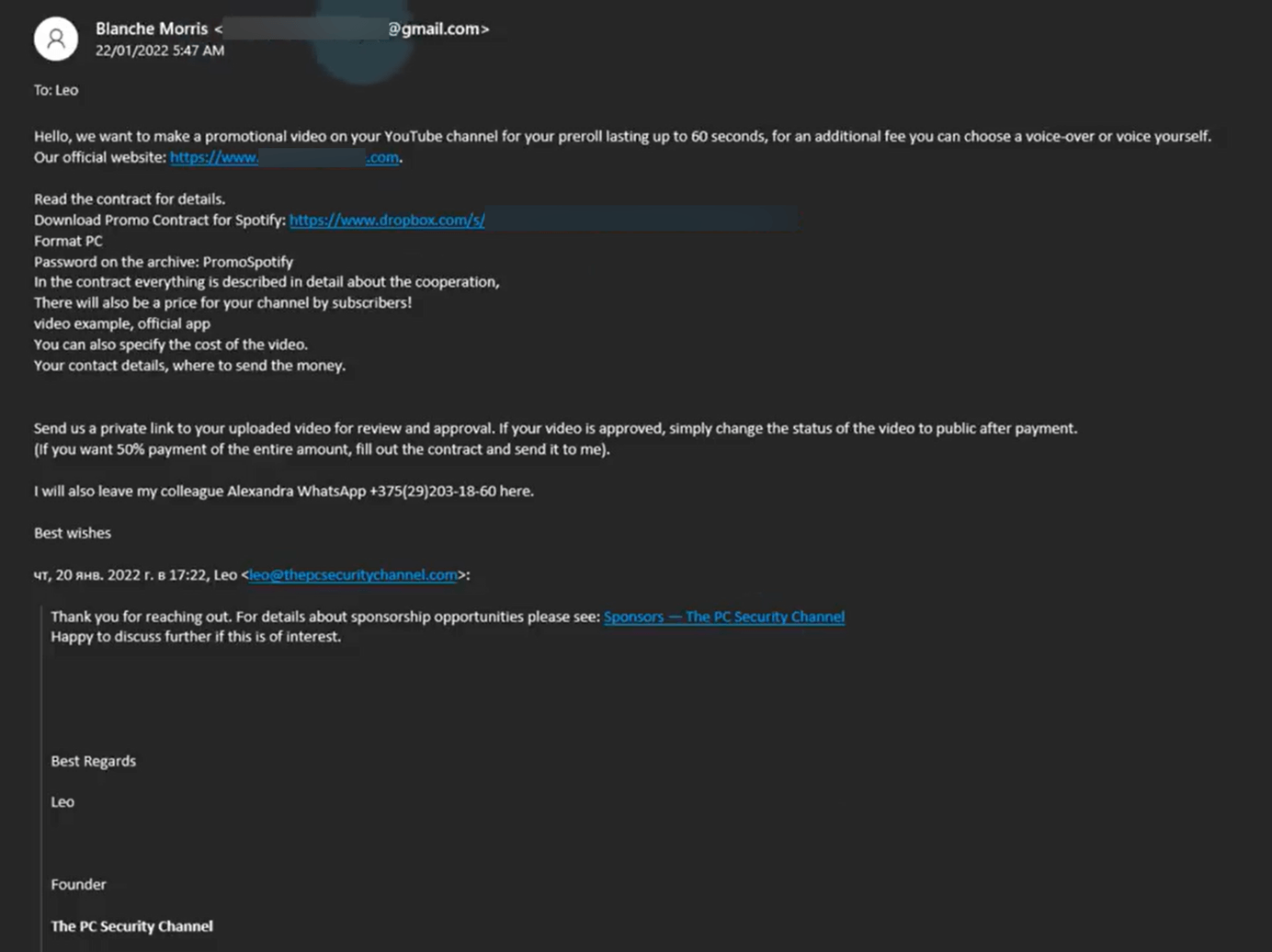
How do they get hacked?
When it comes to the targeting of influencers, attacks begin with the social media account itself – whether it’s X (formerly Twitter), YouTube, TikTok, Instagram or another platform. On rare occasions, the end goal is state-sponsored disinformation. But more often than not we’re talking about financially motivated cybercrime. There are several ways to gain access to accounts, notably:
- Spearphishing: Highly targeted phishing attacks designed to trick the individual into handing over their logins. These may use publicly available information on the target to make them seem more realistic. A phishing email or text could also be booby trapped with a malicious link or attachment, which quietly installs infostealing malware on the victim’s device. It’s another way to get hold of sensitive info like passwords.
- Credential stuffing/brute forcing: Brute-force attacks are a form of trial and error where automated software tries either popular passwords (password spraying) or previously breached passwords (credential stuffing) against large numbers of accounts/websites. When one username/password combo works, they’re in.
- SIM swapping: Hackers socially engineer a telco worker into transferring the victim’s phone number to a SIM under their control. That enables them to intercept two-factor authentication (2FA) codes often used to authenticate and access social media accounts.
It should be noted that AI is helping cybecriminals achieve their goals by crafting more convincing phishing emails in flawless local languages. It also supports campaigns by gathering background information on targets which can be used for these and SIM swapping attacks. And AI can make brute-force attacks faster and more effective.
What happens next?
With access to a high-value influencer account, a cybercriminal might want to sell it immediately online to the highest bidder. Or they could use it themselves. Either way, it’s most likely to be used to advertise crypto investment scams and other get-rich-quick schemes designed to trick followers out of their hard-earned cash. Or to post malicious links which could install malware on followers’ machines.
A threat actor may also try to extort their victim into paying them money to regain access; for example by threatening to post vulgar or inflammatory content. They may be able to access follower contact databases, which could be sold and/or used to target followers directly with spam and phishing attacks. A hijacked account might theoretically also be abused to post false claims about brands connected with that influencer.
If threat actors also manage to compromise an influencer’s e-commerce account (using the same techniques listed above), they may be able to divert incoming funds from followers.
The bottom line is identity theft-related security risks for followers, trashed reputation for brands and influencers, and potentially direct losses for content creators.
Under lock and key
Faced with what could be an existential risk, influencers need a plan of action. That should be based around solid best practices for account security. Consider:
- Long, strong and unique passwords that are harder for password spraying tools to crack.
- App-based 2FA (e.g., apps such as Google Authenticator or Microsoft Authenticator) rather than text-based 2FA codes that can be intercepted. These will ensure that, even if hackers get hold of a password, they won’t be able to access the account.
- Greater phishing awareness; especially some of the lures that hackers typically use to entice influencers, like lucrative seeming sponsorship deals with big-name brands. If something looks too good to be true, it usually is.
- Separate devices and email accounts for work and personal use, with the business ones fitted with higher-grade security controls.
- Security software from a reputable provider on all devices and machines. This should prevent malicious downloads and block phishing emails.
- Always keeping device and PC software/operating system on the latest version, which will mean the most secure version.
- Never downloading apps from unofficial app stores, as they may be harboring info-stealing malware.
An influencer’s reputation ultimately defines their commercial success. It must be protected at all costs.
