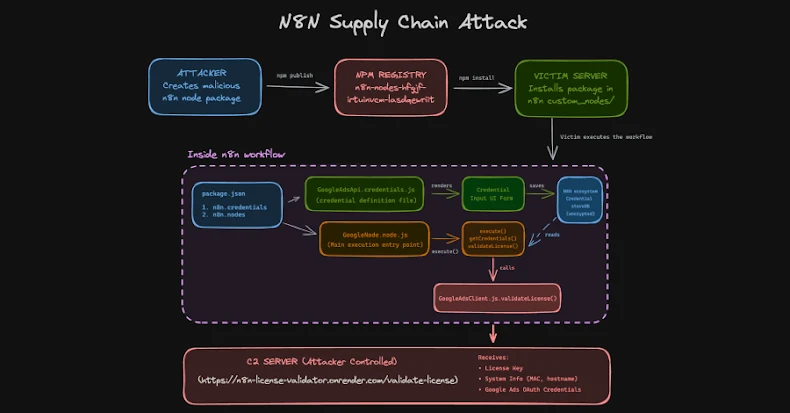
Threat actors have been observed uploading a set of eight packages on the npm registry that masqueraded as integrations targeting the n8n workflow automation platform to steal developers’ OAuth credentials.
One such package, named “n8n-nodes-hfgjf-irtuinvcm-lasdqewriit,” mimics a Google Ads integration, and prompts users to link their advertising account in a seemingly legitimate form and then siphon OAuth credentials to servers under the attackers’ control.
“The attack represents a new escalation in supply chain threats,” Endor Labs said in a report published last week. “Unlike traditional npm malware, which often targets developer credentials, this campaign exploited workflow automation platforms that act as centralized credential vaults – holding OAuth tokens, API keys, and sensitive credentials for dozens of integrated services like Google Ads, Stripe, and Salesforce in a single location.”
The complete list of identified packages, which have since been removed, is as follows –
- n8n-nodes-hfgjf-irtuinvcm-lasdqewriit (4,241 downloads, author: kakashi-hatake)
- n8n-nodes-ggdv-hdfvcnnje-uyrokvbkl (1,657 downloads, author: kakashi-hatake)
- n8n-nodes-vbmkajdsa-uehfitvv-ueqjhhhksdlkkmz (1,493 downloads, author: kakashi-hatake)
- n8n-nodes-performance-metrics (752 downloads, author: hezi109)
- n8n-nodes-gasdhgfuy-rejerw-ytjsadx (8,385 downloads, author: zabuza-momochi)
- n8n-nodes-danev (5,525 downloads, author: dan_even_segler)
- n8n-nodes-rooyai-model (1,731 downloads, author: haggags)
- n8n-nodes-zalo-vietts (4,241 downloads, authors: vietts_code and diendh)
The npm users “zabuza-momochi,” “dan_even_segler,” and “diendh” have also been listed as authors for four other libraries that are still available for download as of writing –
It’s not clear if they harbor similar malicious functionality. However, an assessment of the first three packages on ReversingLabs Spectra Assure has uncovered no security issues. In the case of “n8n-nodes-zl-vietts,” the analysis has flagged the library as containing a component with malware history.
Interestingly, an updated version of the package “n8n-nodes-gg-udhasudsh-hgjkhg-official” was published to npm just three hours ago, suggesting that the campaign is possibly ongoing.
The malicious package, once installed as a community node, behaves like any other n8n integration, displaying configuration screens and saving the Google Ads account OAuth tokens in encrypted format to the n8n credential store. When the workflow is executed, it runs code to decrypt the stored tokens using n8n’s master key and exfiltrates them to a remote server.
The development marks the first time a supply chain threat has explicitly targeted the n8n ecosystem, with bad actors weaponizing the trust in community integrations to achieve their goals.
The findings highlight the security issues that come with integrating untrusted workflows, which can expand the attack surface. Developers are recommended to audit packages before installing them, scrutinize package metadata for any anomalies, and use official n8n integrations.
N8n has also warned about the security risk arising from the use of community nodes from npm, which it said can introduce breaking changes or execute malicious actions on the machine that the service runs on. On self-hosted n8n instances, it’s advised to disable community nodes by setting N8N_COMMUNITY_PACKAGES_ENABLED to false.
“Community nodes run with the same level of access as n8n itself. They can read environment variables, access the file system, make outbound network requests, and, most critically, receive decrypted API keys and OAuth tokens during workflow execution,” researchers Kiran Raj and Henrik Plate said. “There is no sandboxing or isolation between node code and the n8n runtime.”
“Because of this, a single malicious npm package is enough to gain deep visibility into workflows, steal credentials, and communicate externally without raising immediate suspicion. For attackers, the npm supply chain offers a quiet and highly effective entry point into n8n environments.”
Update
In a statement shared with The Hacker News, Endor Labs confirmed that the npm package “n8n-nodes-gg-udhasudsh-hgjkhg-official” is malicious and is part of the same campaign. The remaining packages have been determined to be benign.