If your data is on the dark web, it’s probably only a matter of time before it’s abused for fraud or account hijacking. Here’s what to do.
Contrary to popular belief, much of the dark web isn’t the den of digital iniquity that some commentators claim. In fact, there are plenty of legitimate sites and forums there offering privacy-enhanced content and services to help individuals avoid censorship and oppression. However, the truth is, it’s also a magnet for cybercriminals, who can visit its forums, marketplaces and other sites without fear of being tracked and unmasked.
Many of these exist to facilitate the trade in stolen personal and financial information. Often, personal data is bought and sold alongside other items like narcotics, hacking tools and exploits. So what should you do if you find out your data is up for sale on one of these sites?
How did my data get there?
There are various ways personally identifiable information (PII), credentials and financial data can end up in the hands of cybercriminals:
- Data breaches involve the large-scale theft of customer/employee information, which then usually appears for sale on the dark web. The US was on track for a record year in this area, having already recorded 1,732 incidents in the first half of 2025, leading to over 165.7 million breach notifications. We all do business with so many organizations online these days, the risk of being caught up in a breach is growing all the time. Most of us will have experienced at least one notification email in our lives. That risk also increases thanks to the proliferation of double extortion ransomware attacks, where data is stolen in order to extort a victim organization.
- Infostealer malware does what the name suggests. It has become incredibly popular thanks to “as-a-service” kits like RedLine and Lumma Stealer. The malware can be hidden in legitimate-looking mobile apps, on web pages, in malicious ads, and phishing links/attachments, among other places. The data it collects is then assembled by threat actors and sold on the dark web. Often, both credentials and session cookies are stolen, making it easier for hackers to bypass even multi-factor authentication (MFA).
- Phishing has always been a popular way to steal information from a victim. But the advent of generative AI (GenAI) tools has made it easier for threat actors to scale attacks, while also personalizing them, and writing in flawless local language to increase their chances of success. If you unwittingly click through and enter your information on a phishing site, it could end up being sold on the dark web.
- Accidental leaks are a common occurrence on the internet due often to misconfiguration of cloud systems, such as failing to require a password to access online databases. This can leave data exposed to anyone who knows where to look (or has been scanning for misconfigured instances). If it’s left open for long enough, a database could be stolen and sold on the dark web. Threat actors could also delete the original database in order to extort their corporate victim.
- Supply chain attacks are similar to regular data breaches, but instead of the company you shared your data with being hacked, it is a supplier or partner organization. These companies have been granted permission to access and use that information, but often don’t have the same robust security posture. They are an attractive target for threat actors as just one attack could help them to access data on multiple, corporate clients. Sometimes, these suppliers are digital providers, like Progress Software. When a zero-day vulnerability in its popular MOVEit file transfer software was exploited in 2023, thousands of organizations and over 90 million downstream customers were compromised. Data brokers are another potential weak link. They harvest information legally via web scraping and tracking, but may not keep it well protected.
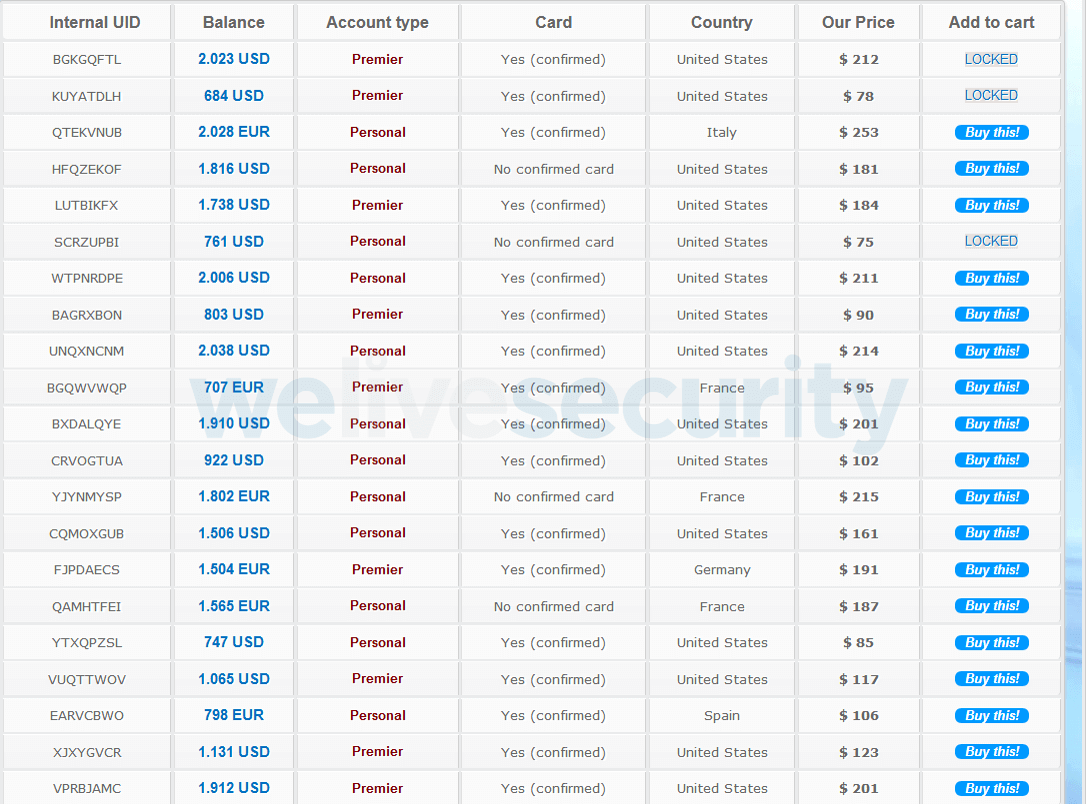
What do they want?
The stuff that cybercriminals really want is your financial information (bank account numbers, card details and logins), PII, and account logins. With this, they can hijack accounts to drain them of data and funds, and possibly access stored card information, or else use your PII in follow-on phishing attempts designed to get hold of financial information. Alternatively, they could use that PII in identity fraud, such as applying for new lines of credit, medical treatment or welfare benefits.
Biometric data is particularly sensitive as it can’t be “reissued” or reset like a password. And session tokens/cookies are also useful for threat actors as these can help them to bypass MFA.
This could have a significant financial impact. A recent ITRC report claims that 20% of US fraud victims over a single year reported losses of over $100,000 and over 10% lost at least $1m.
What to do if you find your information on the dark web
If you’re alerted to the appearance of some personal and/or financial information on the dark web, take the following action (depending on the information at risk):
- Change any compromised passwords, and ensure you only use strong, unique credentials stored in a password manager.
- Switch on MFA for all accounts, and use either an authenticator app or a hardware security key, rather than SMS (which can be intercepted).
- Sign out of all devices, to stop hackers who may have stolen your session cookies.
- Contact your bank, freeze your cards and have them reissued.
- Freeze your credit with each of the main bureaus. This will prevent any fraudster from opening a new line of credit in your name.
- Scan your PC/devices for infostealer malware.
- Report the leak to the FTC (US), Report Fraud (UK) or relevant European authorities.
Long-term steps to keep your PII safe
Once the dust has settled, there are things you can do to mitigate the risk of sensitive information ending up on the dark web. Consider services like Hide My Email to reduce the amount personal information companies store. It’s also a good idea to checkout as a guest and never save any card info when you shop with a third-party site.
Next, reduce the chances of infostealer infection and phishing by installing reputable security software on all of your devices and PCs. Only download apps from official stores. And be wary of any unsolicited emails/texts/social media messages containing links or attachments.
Reduce the volume of data available to brokers by ensuring all of your social accounts are set to “private.” Use encrypted comms services and privacy-enhanced browsers and search engines. Also, consider sending “right to be forgotten” requests to data brokers, possibly via services with the requisite expertise.
Finally, sign up to identity protection services and sites like HaveIBeenPwned, which will alert you when any PII appears on the dark web. The breach of personal information and logins can be emotionally upsetting, as well as financially damaging. And if you reuse logins across work accounts, it could even have a negative impact on your career, if it enables hackers to access corporate resources. At the end of the day, we all need to be proactive in order to make our digital lives safer.
