Details have emerged about a now-patched critical security flaw in the popular “@react-native-community/cli” npm package that could be potentially exploited to run malicious operating system (OS) commands under certain conditions.
“The vulnerability allows remote unauthenticated attackers to easily trigger arbitrary OS command execution on the machine running react-native-community/cli’s development server, posing a significant risk to developers,” JFrog Senior Security Researcher Or Peles said in a report shared with The Hacker News.
The vulnerability, tracked as CVE-2025-11953, carries a CVSS score of 9.8 out of a maximum of 10.0, indicating critical severity. It also affects the “@react-native-community/cli-server-api” package versions 4.8.0 through 20.0.0-alpha.2, and has been patched in version 20.0.0 released early last month.
The command-line tools package, which is maintained by Meta, enables developers to build React Native mobile applications. It receives approximately 1.5 million to 2 million downloads per week.
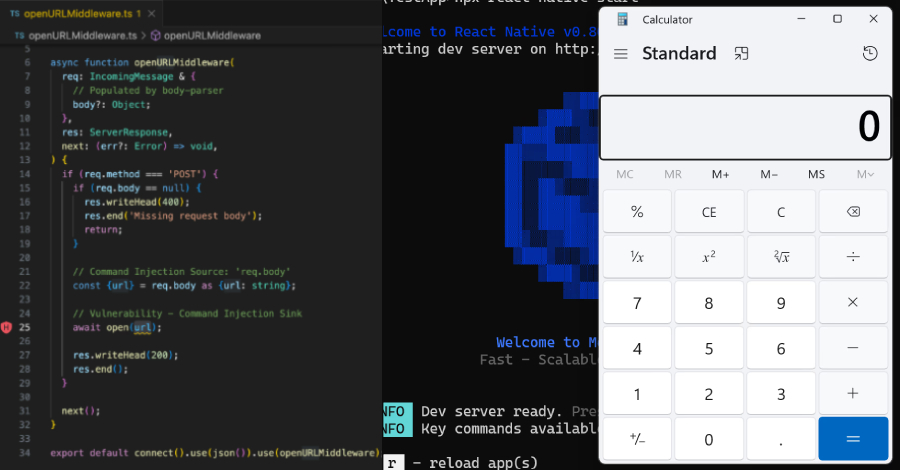
According to the software supply chain security firm, the vulnerability arises from the fact that the Metro development server used by React Native to build JavaScript code and assets binds to external interfaces by default (instead of localhost) and exposes an “/open-url” endpoint that is susceptible to OS command injection.
“The server’s ‘/open-url’ endpoint handles a POST request that includes a user-input value that is passed to the unsafe open() function provided by the open NPM package, which will cause OS command execution,” Peles said.
As a result, an unauthenticated network attacker could weaponize the flaw to send a specially crafted POST request to the server and run arbitrary commands. On Windows, the attackers can also execute arbitrary shell commands with fully controlled arguments, while on Linux and macOS, it can be abused to execute arbitrary binaries with limited parameter control.
While the issue has since been addressed, developers who use React Native with a framework that doesn’t rely on Metro as the development server are not impacted.
“This zero day vulnerability is particularly dangerous due to its ease of exploitation, lack of authentication requirements and broad attack surface,” Peles said. “It also exposes the critical risks hidden in third-party code.”
“For developer and security teams, this underscores the need for automated, comprehensive security scanning across the software supply chain to ensure easily exploitable flaws are remediated before they impact your organization.”